Identity Fraud Ring is a group of fraudsters that works together to commit identity fraud. These criminals operate on a larger scale. This differs from individual identity theft, in which a single scammer steals identities. In identity fraud rings, the organized group coordinates and uses complex plans that are harder to detect and catch. The group can use stolen identities or create fake identities to open bank accounts, get credit cards and loans, buy things, and use medical services.
The impact? Businesses deal with unauthorized transactions, money loss, and damage to trust and reputation.
Identity fraud rings do more harm and are particularly crucial to stop due to their organized nature and the scale of their operations. Thus, fraud ring detection is crucial.
What is an Identity Fraud Ring?
Identity fraud rings are organized groups that illegally obtain and exploit personal information.
These groups either use stolen identities to commit fraud for direct financial gain. Or, at times, they use the data to create fake (synthetic) identities.
- Stolen identity rings steal personal information through data breaches, phishing, or theft. They impersonate victims to make transactions, open fake accounts, or get loans, harming individuals and institutions financially.
- Synthetic identity rings mix real data like social security numbers with fake details to create new identities. They build credit histories for these identities, use them to secure loans and credit cards, and eventually max out the credit in a ‘bust-out’ scam.
Read more about synthetic identity fraud.
These rings are often highly organized and share resources. Their members play specific roles. Some are dedicated to stealing and gathering personal information. Others are for creating fake documents, and some are for committing financial fraud. And so on.
Numbers speak:
- 23.9 million people were victims of identity theft in 2021 (Bureau of Justice Statistics).
- A single fraud ring allegedly stole over $11 million from its victims (report from United States Attorney’s Office).
Read more about identity theft statistics
Types of Fraud Rings
These rings often specialize in specific types of fraud, leveraging coordinated tactics to exploit vulnerabilities. Understanding the diverse nature of these fraud rings is the first step in fraud awareness. This knowledge can empower you to spot risk at the earliest.
Identity Theft Fraud Ring
Here, an organized team of criminals work together to steal personal and financial information. These groups get personal details through phishing, data breaches, and stolen documents. Some of the types of thefts in this fraud include financial identity theft (get credit, goods, services, benefits), social security identity theft (get SSN), medical identity theft (get free medical care and prescription drugs), and synthetic identity theft (create fake identities).
Credit Card Fraud Ring
This group of criminals works together to steal and misuse credit card details. They often plan large-scale attacks to collect card details, such as hacking into retail payment systems or intercepting online transactions. Once they have the data, members of the ring either use the credit card details directly for unauthorized purchases or create counterfeit cards.
Fraud rings can also obtain credit cards using stolen or synthetic identities. In some instances, they enhance the credit scores of these credit card numbers of fake identities by providing fabricated information to credit bureaus. This allows the bogus identities to qualify for large loans and lines of credit, which they convert into cash and never repay.
Insurance Fraud Ring
Insurance fraud rings commit insurance fraud in innovative ways. They have a number of schemes targeting different aspects of everyday life—automobiles, healthcare, and housing are common targets. These rings often involve professionals such as doctors, auto repair technicians, building contractors, and lawyers, who all play roles in executing fraud.
One prevalent method is staging automobile accidents for fake claims. In such scenarios, fraudsters orchestrate collisions to create fraudulent insurance claims. Here’s how they operate:
- The accident usually involves at least one fraudster colliding intentionally with another vehicle, often driven by a co-conspirator, to file multiple claims.
- Following the staged accident, accomplices such as doctors and auto repair technicians exaggerate the damage or injuries. Doctors might bill for unnecessary medical tests or diagnose nonexistent soft-tissue injuries like whiplash, which are hard to disprove objectively.
- Similarly, auto repair technicians might claim pre-existing vehicle damage as new or deliberately cause more damage to inflate repair claims.
This type of fraud not only impacts insurance companies but also leads to higher premiums for all policyholders.
Check Fraud Ring
Check fraud rings operate by forging checks or altering genuine ones to obtain funds illegally. These groups exploit the vulnerabilities in check processing systems.
- Fraudsters can steal checks from mailboxes or trash bins.
- They also use advanced methods to change details on checks like the payee’s name and amount.
- Sophisticated rings possess the equipment to manufacture counterfeit checks that appear authentic.
- Once altered or counterfeited, these checks are deposited into bank accounts under false identities.
Unemployment Fraud Ring
Unemployment fraud rings falsely claim benefits meant for those out of work.
- Fraudsters use the stolen identity information to file claims. They direct the payments to accounts they control.
- In some cases, they infiltrate accounts of actual welfare recipients and reroute their payments to fraudulent accounts.
These rings inflict tremendous damage to the public, as well as businesses.
Top 6 Methods to Detect and Prevent Identity Fraud Rings
As the cases of identity fraud rings rise, it is important for you to take measures. Here are the top six methods for fraud detection and prevention to consider.
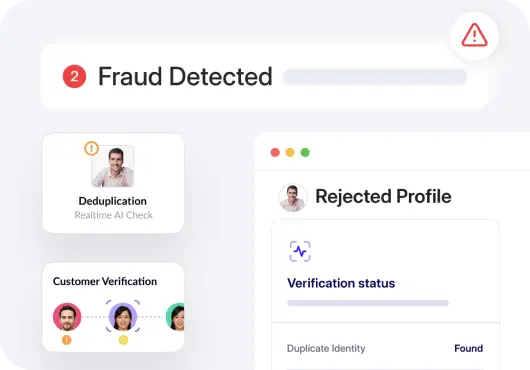
1. Employ a trustworthy AI solution for fraud detection
Artificial intelligence (AI) analyzes patterns to identify any anomaly. This helps detect fraud ring activity early. These systems also deploy intelligent identity verification to fight digital fraud. Invest in a reputable AI solution that is accurate and has good real-time monitoring.
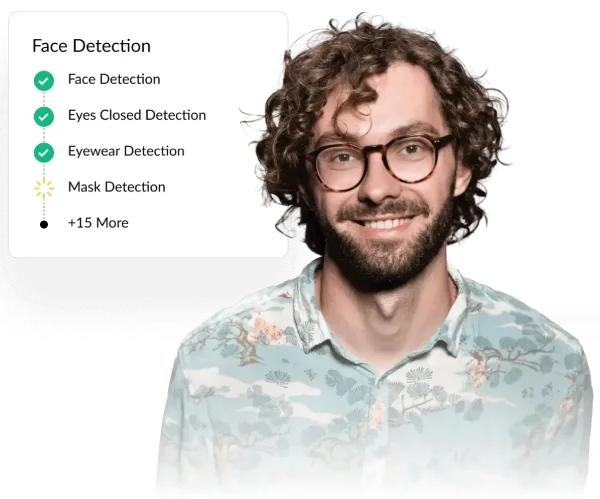
2. Perform biometric verification
Biometric verification uses characteristics like fingerprint, facial recognition, voice identification, iris for verification purposes. This method makes sure that the person accessing the service is who they claim to be.
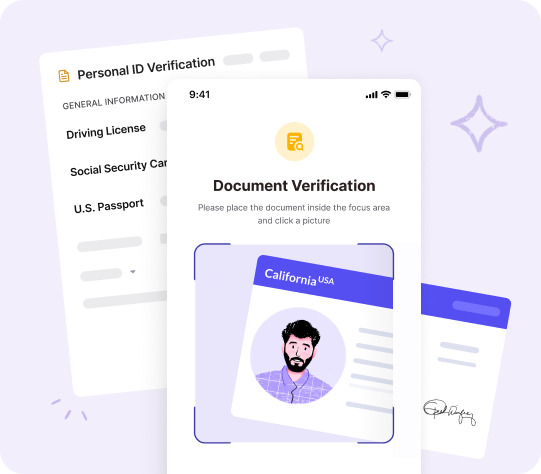
3. Implement document verification
Document verification systems validate the authenticity of ID documents. These systems match details against official databases and also check for security features in documents such as passports or driver’s licenses to ensure they have not been forged or tampered with.
Read more in our ultimate guide to document verification.
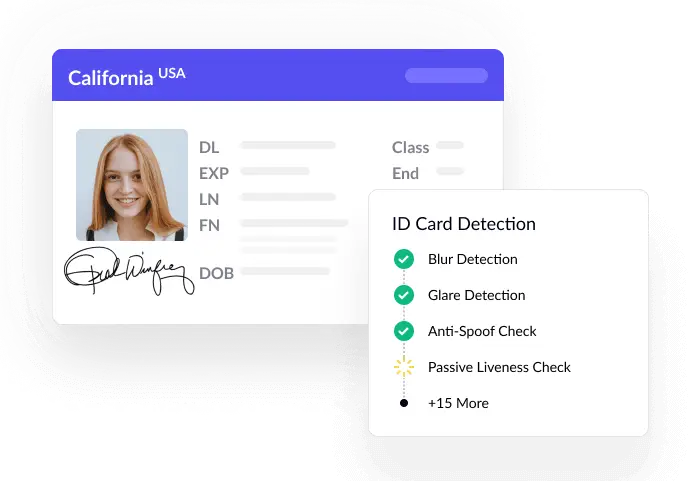
4. Use face authentication with liveness checks
Facial recognition technology checks unique features of a person’s face to confirm their identity. Liveness checks make sure the person is actually there.
5. Continuous transaction monitoring
This means real-time surveillance of accounts and transactions to flag unusual activities. Transaction monitoring helps detect inconsistencies that can mean an account is at risk.
6. Conduct review audits on a regular basis
Review and assess the effectiveness of existing fraud prevention measures regularly. It helps spot any potential weaknesses in the system and ensure compliance with regulatory standards.
Automated AI solutions to identify fraud rings
AI-powered ID verification and KYC solutions play a crucial role in detecting identity fraud rings and other fraud activity. By analyzing patterns and data inconsistencies, these tools quickly identify suspicious activities that might otherwise go unnoticed. This rapid detection helps you prevent potential financial damage and safeguard your reputation. For a more secure future, integrate advanced identity verification technologies into your systems.
Ready to enhance your security with an identity verification solution? Explore our solutions at HyperVerge and sign up to get started at HyperVerge.





