Is that ‘great deal’ costing you more than you think?
Ever signed up for a discount using a new email, even though you’re not exactly a new customer? Or referred yourself for a bonus? You’re not alone.
Businesses use promotions to attract and retain customers. But some people take advantage of these offers—creating fake accounts, exploiting loopholes, or abusing referral programs. This isn’t just a small issue; it’s a growing problem called promotional abuse.
For companies, it means losing money, skewed data, and wasted marketing budgets. For genuine customers, it leads to stricter rules, fewer discounts, and less generous offers. So, how do businesses spot and stop promotional fraud without hurting real users? And why does this matter to you?
In this article, we’ll break down how promotion abuse works, its consequences, and actionable strategies to prevent it.
What is promotion abuse?
Promotion abuse is when someone exploits or misuses promotional offers, discounts, or rewards programs in ways that violate their intended purpose. Such coupon or discount abuses have several negative implications for businesses. For instance, creating multiple accounts to claim ‘new user’ bonuses repeatedly, or finding loopholes to stack discounts that weren’t meant to be combined.
It’s a conscious attempt to gain an unfair advantage from promotional programs beyond their intended legitimate use.
Often, attackers attempt promotion abuse by tapping into the weaknesses of the organization’s identity verification and AML checks. Fraudsters use synthetic identities or stolen credentials to create multiple accounts.
They might also launder money, exploit referral bonuses, or mask illicit funds within legitimate-appearing promotional frameworks. This undermines the integrity of AML compliance and leads to certain undesired consequences.
- The consequences of promotion abuse
Promotion abuse inflicts severe financial damage beyond direct losses from fraudulent discounts. While excessive use of referral and discount codes accumulates huge losses, the reputational cost hits harder.
Plus, legitimate customers lose trust when they can’t access promotions due to tightened restrictions. Business operations suffer as teams divert resources to fraud prevention. Meanwhile, customer support staff gets overwhelmed with complaints.
Further, if a promotion abuse incident goes viral on social media, brands can face backlash from both frustrated as well loyal customers and investors questioning their security measures.
How promotion abuse works?
Attackers often employ common tactics and patterns to attempt promotion abuse. Let’s understand them.
- Creating fake accounts
Fraudsters often create multiple email accounts and use fake phone numbers to register multiple times for new user bonuses. For example, exploiting a ‘$10 off first order’ by creating dozens of accounts.
- Exploiting referral programs
Abusers create fake ‘referee’ accounts to collect referral rewards from their main account. Suppose a skincare brand offers a $20 gift card per successful referral. Abusers exploit this opportunity by inviting fake users to get $20 per referral and then cashing out the rewards.
- Abusing promo code
This involves trying to reuse one-time codes multiple times or sharing private/targeted codes publicly. An example, imagine a targeted ‘VIP50’ code meant for select customers getting shared on deal sites.
- Account takeover
Fraudsters may gain access to legitimate accounts (often via credential stuffing) to use stored payment methods, points, or member benefits. They may drain reward points or make unauthorized purchases.
- Exploiting vulnerabilities in verification processes
Exploiting gaps in identity verification includes using temporary phone numbers for SMS verification. Some abusers might submit fake addresses or documents for ID checks.
- Using bots to automate abuse
Abusers may use automated scripts to mass-create accounts or test promo codes at scale. For instance, bots can be employed to check gift card balances.
- Synthetic identity fraud
Fraudsters may combine real and fake personal information to create plausible fake identities for promotions requiring verification.
- Manipulating geolocations to circumvent restrictions
Criminals may use VPNs or GPS spoofers to appear to be in different locations to bypass geographical restrictions. This way, they access region-specific promos. Some of them might also claim local deals multiple times.
- Other methods
At times, abusers may utilize stolen personal information from the dark web or data breaches to create synthetic identities with valid SSN formats. Using temporary phone numbers for SMS verification is another common tactic.
Abusers can also evade AML screening by structuring transactions below reporting thresholds. Then, they layer them across multiple accounts, often using shell companies as fronts. Additionally, they mask their true location using VPNs, emulate devices, and manipulate browser fingerprints to appear legitimate.
Identifying signs of promotion abuse
Identifying promotion abuse signs is the first step to preventing them. Let’s break down potential signs that abusers may leave—
- A high volume of new account creations
Let’s say a business offers generous first-time user discounts (e.g., ‘$25 off first order’). Fraudsters might create hundreds of new accounts in short periods to exploit this discount.
- Frequent use of promo codes from the same IP address
Suppose a clothing retailer offers a ‘20% off’ promo code intended for one-time use. They find single IP addresses attempting to use the same code hundreds of times in hours. The transactions were happening from different accounts linked to the same payment method.
- Multiple accounts with similar information
Consider the case of a ride-sharing app. Abusers might create dozens of accounts using slight variations of the same details:
- Email: john.smith1@gmail, john.smith2@gmail
- Phone: sequential numbers differing by the last digit
- Address: apartment numbers incremented sequentially
These accounts will all be linked to the same payment methods. By doing this, an abuser can avail first-time ride discount multiple times.
- Unusual geographic activity/VPN use
A major streaming service detected that some accounts are accessing their platform from 10+ different countries. That too within a few hours. This is technically impossible for legitimate users. Investigation revealed fraudsters were using VPN services to claim region-specific promotions multiple times.
- Rapid, repetitive transactions/logins
Let’s say a food delivery platform noticed accounts placing orders every few minutes—far faster than humanly possible to consume meals. This indicates a possibility of automated bots exploiting a ‘50% off next order’ promotion, reselling discounted orders.
- A significant spike in referral bonuses
An unusual spike in referral bonuses should raise alarm. For instance, a user may have created fake referee accounts using stolen identities to claim bonuses.
- Inconsistent user behavior compared to normal patterns
Consider an e-commerce platform noticing accounts with unusual purchasing patterns. Where normal users browse multiple items, add/remove from the cart, and purchase occasionally, abuse accounts could be directly navigating to specific items and making instant purchases, without browsing. Such patterns reveal that attackers may be using automated systems to exploit promotions.
- Multiple failed verification attempts
At times, businesses notice accounts attempting verification 5,10, or 20+ times with slightly modified documents. Such activity signals attackers who systematically test which modifications could bypass the organization’s verification system to claim new user bonuses.
Mitigating promotion abuse risks
The below strategies can help businesses prevent promotion abuse risks better.
- Implement robust identity verification processes
Your identity verification must go beyond basic KYC. Leading platforms like HyperVerge now implement dynamic document verification frameworks.
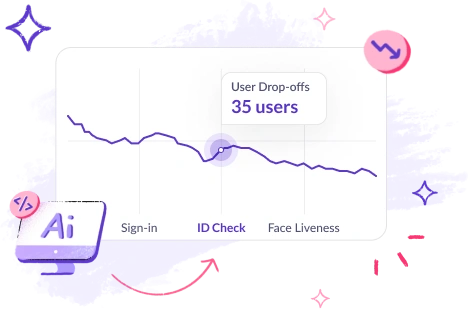
This involves analyzing micro-features in submitted IDs, cross-referencing multiple data points, and using advanced OCR to detect manipulated documents.
- Leverage liveness detection for account verification
As deepfakes and synthetic identities take over, sophisticated liveness detection has become paramount. Adopting advanced systems incorporating micro-movement analysis, depth mapping, and reflected light patterns is paramount to ensure a real person is present during verification.
For instance, individuals creating accounts through faces in videos or images, instead of live faces, are flagged during verification.
- Utilize multi-factor authentication (MFA)
Modern MFA goes beyond simple SMS codes. Businesses need to implement risk-based authentication that adjusts security levels based on user behavior, location, and transaction value.
Organizations can enforce more controlled abuse prevention through adaptive MFA. This requires additional verification steps when unusual patterns, such as new device usage or suspicious IP addresses, are detected.
- Adaptive MFA
Adaptive MFA, a dynamic security approach intelligently adjusts authentication requirements based on real-time risk assessment. Unlike traditional static MFA, adaptive systems analyze multiple risk signals.
When suspicious patterns emerge, the system automatically escalates security requirements. For example, a user logging in from their regular device might only need basic verification. However, the same user attempting a large transaction from a new location would trigger additional authentication steps like biometric verification or security questions.
- Monitor for unusual patterns and anomalies
Advanced pattern recognition now incorporates machine learning models that analyze hundreds of data points in real-time. These systems look for subtle correlations between seemingly unrelated accounts and transactions.
For instance, a food delivery app can uncover a fraud ring by detecting minute similarities in typing patterns, order timing, and delivery locations across thousands of apparently unrelated accounts.
- Set limits on promo code usage per user/IP address
Modern promotion engines implement dynamic usage limits based on user behavior and risk profiles. Rather than simple static limits, these systems use AI to establish normal usage patterns and flag deviations.
Businesses can repel risk by adjusting smart limits based on customer history, purchase patterns, and risk scores.
- Conduct regular audits of referral programs
Advanced referral program auditing now uses network analysis to map complex relationships between accounts and identify coordinated abuse. These systems analyze patterns in referral chains, timing of signups, and shared characteristics to detect fraud rings.
Businesses can identify abuse by mapping subtle connections between seemingly unrelated referrers.
- Integrate real-time AML checks
Modern AML tools like HyperVerge operate in real time, analyzing transactions and user behavior against constantly updated risk models. These platforms use AI to detect subtle patterns indicative of promotional abuse.
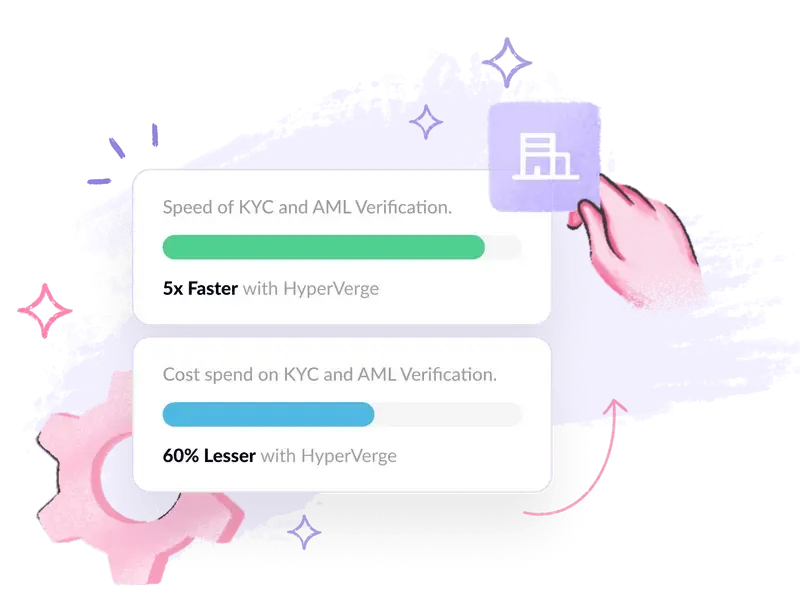
For instance, payment platforms can prevent fraudulent transactions by implementing real-time AML checks that could identify structured transactions designed to exploit promotional offers.
- Deploy AI and machine learning for fraud detection
State-of-the-art fraud detection systems now use ensemble learning approaches, combining multiple AI models to analyze different aspects of user behavior. These systems can detect subtle patterns invisible to human analysts.
- Block access from known VPNs or proxies
Advanced VPN detection goes beyond simple IP blacklisting. Modern systems use machine learning to analyze traffic patterns, browser fingerprints, and network characteristics to identify VPN usage.
- Use behavioral analytics to identify suspicious activity
Modern behavioral analytics incorporate keystroke dynamics, mouse movements, and session patterns to create detailed user profiles. These systems can detect automated tools and unusual behavior patterns with high accuracy.
For instance, a leading online platform reduced bad actors and improved document validation accuracy by 30%, after going live with Hyperverge. They avoided fraud by flagging high-risk users while onboarding. The tool helped them check each individual’s data against the central database in seconds.
Best practices for identity verification
Building a comprehensive identity verification involves integrating various components and tools into a seamless verification flow.
Here are the best practices to build the same-
- Multi-layered security approach
A multi-layered approach to identity verification serves as the strongest defense against sophisticated promotion abuse.
- Start with automated document verification that analyzes subtle security features in IDs while checking for manipulation.
- Advanced OCR technology now reads and verifies document content against issuing authorities in real-time, while checking for internal consistency across all document fields.
- Follow this with biometric verification, requiring users to match their selfie to their ID photo and complete dynamic liveness checks.
Automated identity verification and AML tools like HyperVerge help you build seamless multilayered defense mechanisms against promotion abuse fraud. You create customized workflows and incorporate them into your organization’s existing operations through APIs.
- Monitor user behavior
Businesses must track and analyze user behavior continuously, not just at specific checkpoints. Advanced behavior analytics engines scrutinize every user interaction—from mouse movements to transaction patterns—creating detailed behavioral fingerprints that instantly flag anomalies.
Attackers often expose themselves through velocity patterns. Such patterns are attempting multiple verifications within minutes, creating accounts in rapid succession, or processing transactions faster than humanly possible.
- Incorporate risk-based workflows
Risk-based workflows automatically assign specific verification routes to users. A low-risk user with consistent device fingerprints and normal behavior patterns might only need basic checks, while suspicious patterns may trigger enhanced verification requirements.
For instance, in case of high-risk transactions, businesses can implement manual expert review as a final checkpoint. Trained analysts can spot subtle discrepancies that automated systems might miss.
Implementing strong AML measures
Anti-Money Laundering (AML) compliance prevents promotion abuse by ensuring that businesses identify and stop suspicious activities before they escalate. When companies implement AML measures, they monitor transactions and user behaviors for signs of fraud. They can recognize when someone tries to exploit discounts or large amounts of money are being funneled through promotional offers.
Monitoring these activities enables businesses to detect potential abuse early on. Here are the key components of an effective AML compliance program for combating promotional abuse:
1. Know your customer (KYC)
KYC is the foundation of any AML program. It involves verifying the identity of customers during onboarding and requires continuous monitoring further. This includes collecting information about their financial activities, geographic locations, and transaction patterns.
For instance, a fintech company might identify users who frequently change their payment methods or use multiple accounts, a tactic often used to exploit referral software incentives. This is how continuous assessments pinpoint potential abuse of promotional offers.
2. Risk assessment
Conducting regular risk assessments helps organizations identify vulnerabilities related to promotion abuse. By evaluating customer behaviors and transaction types, companies can prioritize which customers require enhanced scrutiny.
For instance, a subscription-based platform can assess users based on their referral patterns and flag those with suspicious activity for further review.
3. Transaction monitoring
Continuous monitoring of transactions is crucial in detecting unusual patterns indicative of fraud. Advanced algorithms can analyze transaction data in real time to identify red flags.
Multiple accounts linked to a single IP address attempting to redeem the same promotional offer can be a sign of abuse.
4. Enhanced due diligence (EDD)
For high-risk customers identified during the KYC process, EDD measures are necessary. This involves gathering additional information and conducting thorough investigations.
Suppose a user is flagged for using multiple accounts to exploit discounts. Then EDD would require a deeper analysis of their transaction history and referral activities.
5. Suspicious activity reporting (SAR)
When suspicious activities are detected, filing SARs with relevant authorities is essential for compliance and investigation purposes. This process helps in tracking potential attackers. It also serves as a deterrent for would-be abusers aware that their actions are being monitored.
6. Employee training
An effective AML program is incomplete without a well-informed workforce. Regular training sessions should educate employees about identifying signs of promotion abuse and understanding the importance of compliance measures.
For instance, customer service representatives trained to recognize unusual account behaviors can help prevent fraud.
7. Independent audits
Regular independent audits make AML protocols effective and compliant with regulations. These audits can reveal gaps in processes or areas where promotion abuse may be slipping through the cracks. Organizations can adapt their strategies accordingly.
8. Technology integration
Leveraging technology solutions, such as machine learning and AI, enhances the ability to detect and prevent promotion abuse. Tools that analyze customer behavior patterns can provide insights into potential fraudulent activities.
Implementing this comprehensive approach protects financial integrity, fosters trust among legitimate customers and creates a safer environment for all stakeholders involved.
Protecting your business from promotion abuse
Layered verification coupled with a strong AML process is an undefeated defense mechanism against promotion abuse. It filters out bad actors right at the onboarding stage.
Hyperverge offers advanced AML solutions that help businesses unlock growth without the concerns of losing revenue and reputation to promotion abuse incidents.
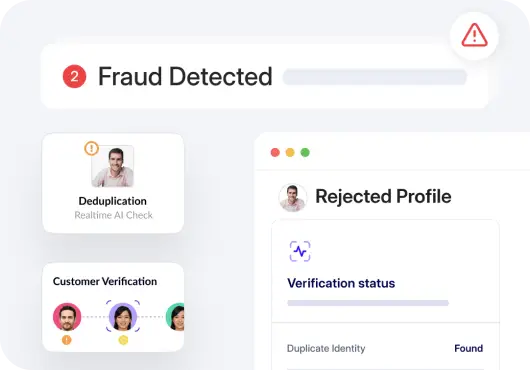
Explore powerful tools to balance your identity verification with compliance, security, and smooth customer experience.
Schedule your demo today. Protect your business from fraud without experiencing friction.
FAQs
1. How to prevent promo abuse?
Key solutions to prevent promo abuse include an enhanced verification process, monitoring user behavior, creating unique codes, limiting redemption opportunities, outlining strict terms and conditions, and educating customers.
2. What is an example of promo abuse?
An example of promo abuse is when individuals create multiple fake accounts to repeatedly claim sign-up bonuses or discounts intended only for new customers.
3. What is discount abuse?
Discount or bonus abuse refers to the intentional exploitation of promotional offers, such as coupons or discounts, by customers. Abusers try to gain unfair benefits by creating multiple accounts or sharing codes.
4. What is an example of sales promotion abuse?
An example of sales promotion abuse is a group of individuals sharing a single promotional code among themselves. This allows them to exploit a discount meant for individual use.
5. Is promotion abuse illegal?
Promotion abuse is considered illegal, particularly when it involves fraudulent activities such as creating fake accounts or misrepresenting eligibility to exploit discounts. Businesses may pursue legal action when the abuse results in significant financial loss or violates consumer protection laws. However, enforcement can vary, and not all instances lead to criminal charges.





