Cardholders are quite happy with credit cards, in most cases. Any loss due to an unauthorized transaction on their card is reversed back to them at no cost by their bank. They need to provide only very reasonable evidence. And who is penalized for such a loss? The loss arising from credit card fraud is in most cases diverted back to the merchant who administered the fraudulent transaction. As unfair as this seems, this is the reality. The merchant pays for the negligence or misfortune of the cardholder. However, even though life is easier for a cardholder in case of fraud, there is no denying the fact that it does cause quite a bit of heartburn for everyone involved in the loss, the cardholder, the bank, and of course the merchant. Everyone wishes there was better credit card fraud detection tools.
How does credit card fraud occur?
There are only two possibilities:
(1) A hacker or thief gets hold of a person’s credit card details
In such a case, the thief has actually managed to secure not just the credit card number but the CVV, the name of the cardholder, and the expiry date of the card as well. The thief or hacker can then use these stolen credit card details for online fraudulent transactions.
(2) The cardholder did the transaction but denied it later
This is a case of friendly fraud and it is hard to detect. In this case, the cardholder has carried out the transaction but denies having done so. An actual investigation needs to be carried out by the banking institution and all other possibilities have to be ruled out before the inquiry moves to the customer.
Types of credit card frauds
Every day thousands of credit card numbers are bought and sold on the darknet. According to sources, the lowest price can be as low as $8 and can go up to just $15. The payments are almost always made through Bitcoin. Assuming that there has been an actual theft of credit card information, let’s look at different types of fraud:
Theft
The first method is the good old straight-up mug job, where you pickpocket and get physical possession of the credit card. Certain contactless payments may not need any kind of pin or OTP and this gives criminals the opportunity to use them directly for a purchase or even to pay hefty bills.
Skimming and Cloning
Credit card fraudsters make use of special machines called skimmers to get the credit card information of a person. These skimmers are generally installed on top of a regular card reader and are difficult to distinguish when placed on top. Once the details are secured, it can be used to make fraudulent purchases online, much as is done in the case of a theft.
According to a Nielsen Report, cardholders lose about $28.65bn per year to skimming and cloning of credit cards.
Account Takeover
If a person gains unauthorized access to an account, then they can easily siphon off the money that is present in the account. But what if there is also a credit card that is linked to that account? In such a case, a hacker can easily take over the credit card as well and initiate fund transfers using the money on the credit card. And if they gain access to an e-wallet, then the problem is even worse, with hackers being able to access or transfer funds directly, as there is no additional layer of security.
Phishing/Social Engineering
In phishing, emails or SMS are sent out to those who hold credit cards, making it seem like it originated from a genuine and trustworthy source. These emails generally tempt the user to make a payment citing that it has been a while that the user has used the credit card or that there is a special offer at a merchant that will fetch an additional discount or cashback. In advanced phishing, the criminals set up unsecure bank pages that mimic the actual banking website. Once the unsuspecting user enters the details they are relayed back to the hacker and then the funds are transferred to the hacker’s account. This is not all. There could be fake online shops, entire e-commerce websites that do not actually ship anything and are created with the sole purpose of securing the customer’s credit card details.
What happens in social engineering? Actual people are used in this credit card fraud. The customer is contacted by a person who claims to be someone close, such as a friend of a friend or a former colleague’s acquaintance or even distant family. The person would have prepared thoroughly for the job having stolen data from the user’s social media or mail accounts and seem very convincing. They would then bring up a need or requirement and get the user to perform a transaction with them on the line or reveal their credit card details directly.
Infiltrating Legitimate Online Shops
The hacker can infiltrate online shops that are legitimate and have a good number of buyers. All they need to do in such a case is to run a script that will be injected into the app or the website, get access to credit card information as users purchase and then relay the information back to themselves. Then fraudsters can use stolen identities to siphon out large amounts of cash from individual accounts.
Methods to detect credit card frauds
Fraudsters have many techniques at their disposal to get hold of credit card information. So agencies that track these criminals and banking institutions must have equally tight measures in place.
Card Security Features
Several card security features are built into a credit card to ensure that the card information does not fall into the wrong hands.
Address Verification Service(AVS): Address verification is carried out initially to ensure that the cardholders address and the address on record match. This will ensure that the card has not been stolen.
3-D Secure (3DS): This is a layer of security that prompts users to enter a code, otherwise the purchase is void. Visa Secure from Visa, SecureCode from Mastercard, or SafeKey from American Express are some examples.
CVV: The CVV is a three-digit number that is located at the back or at times the front of the card. This code helps confirm that the card is in possession of the cardholder at the time of the transaction.
These card security features are great, but they unnecessarily slow the customer down during the purchase process and thereby hamper the customer experience. So e-commerce sites such as Amazon today generally do not require a customer to enter the CVV over and over. If it has been entered once, then it is okay. Amazon has other measures in place such as a protected customer login process to ensure that the right person gets access to profile details. Anyway the CVV is always dotted out and not visible to anyone.
Risk Scoring
It is a standard method used to detect credit card fraud. There are certain predefined rules that determine whether a particular user must be granted access based on the scenario that he/she finds himself in. Based on the risk score and transaction history, if the transaction does not look suspicious then it is allowed else it will be blocked.
Risk scoring is based on heuristics (If-then logic). It is basically a set of conditions where if the user satisfies a certain clause then they would be allowed access to the credit card, else no. An instance of a simple heuristic based risk scoring is:
If the IP address is the same as the shipping address, allow access, else no.
An advanced instance of risk scoring would be the velocity rule. A simple example of this is:
If the user enters the incorrect password five times in less than an hour, then the account will be temporarily blocked. This is because such an activity seems similar to a brute-force hack attempt.
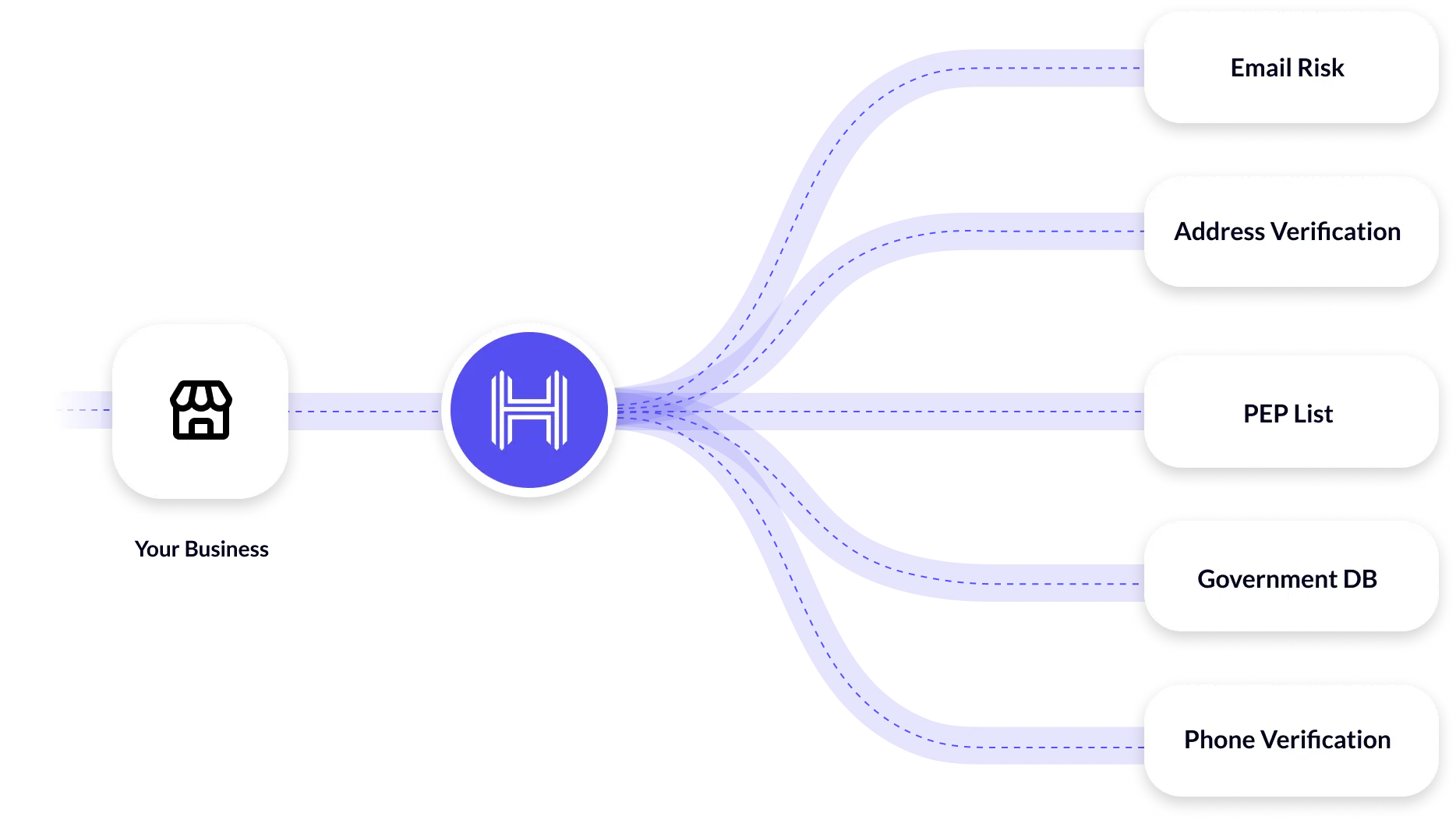
Essential tools for credit card fraud detection
For credit card fraud detection, the best technology available is ML (machine learning) and the tools associated with it such as Python, associated libraries and Jupyter notebooks. The challenges for developing a fraud-identifying model are:
Enormous data has to be processed on a daily basis as credit cards offer discounts, cashback and installment options, which encourage people to use them.
Most of the transactions are fair and only very few(less than 0.1% generally) are fraudulent. To identify such a small number of frauds, conducting extensive and costly fraud detection systems may not be worth it.
Data available may be private and confidential. There may not be access to such data, so the model cannot work.
Scammers often employ adaptive methods against the model used for detecting frauds and the model cannot be updated each time.
The fraud detection model built on Python though has two main benefits:
- It can be modified easily with help from the Python community
- It is not complicated to maintain and is quite scalable
Several identity verification companies such as HyperVerge also offer credit card fraud detection solutions. Contact us to know more.
Prevention of credit card fraud
Credit card fraud can be prevented by making sure you:
- Use a reliable credit card fraud detection systems to block fraudulent transactions
- Carry your credit card safely in an NFC hack-proof wallet
- Do not hand over the credit card at a public place to complete a transaction
- Do not voice your credit card details esp. CVV over the phone even to customer service
- Do not share your 3-D secure code or pin with anyone else, even if they request it
- Do not share the address or other security information provided for your credit card
- Set daily transaction limits on your credit card to avoid a large sum being withdrawn
- Set fraud alerts where you will get notification for any suspicious transactions
Closing words
Credit card fraud detection is the need of the hour. Companies like HyperVerge are doing their bit to ensure that they stay ahead of the game and catch hold of the criminals in time. Are you looking for any kind of credit card fraud detection help? HyperVerge provides a fraud detection and compliance-focused identity verification system that can help you with credit card fraud detection.
FAQs
Does your bank know who stole your credit card?
Credit card companies are able to monitor any transactions made on your card even after it is stolen, and they would be able to track its use anywhere by the person who stole it.
Will banks refund scammed money?
Contact your bank immediately if you have been scammed. Provide the bank the transaction ID and request the bank for a reimbursement. If you are in the UK, most banks should reimburse the money.
What can someone do if they know your credit card number and CVV?
They would also need to know the expiry date of your code to make an online purchase.
If your card is stolen, can the person make in-store purchases?
When making an in-store purchase, a swipe of the physical card alone is sufficient, but the thief would also need to know your PIN