Taking and verifying a selfie is a simple yet effective way for businesses to verify legitimate users and protect their assets through AI-driven biometric analysis.
Selfie verification, a blend of convenience and technology, is being harnessed to reauthenticate returning customers and build a secure digital economy. During the selfie verification process, a user is typically asked to take a selfie or a video to demonstrate liveness, which is then compared against an ID document, adding a robust layer of defense against unauthorized access and deepfakes.
In this guide, we’ll cover the steps for accurate selfie identity verification, including liveness detection and best practices. Let’s begin!
What is selfie identity verification?
Selfie identity verification, often termed selfie authentication, is a biometric process. It uses a person’s unique facial features as a way to confirm their identity.
Here’s how it works: a user takes a selfie, which is then matched against a photo ID document, like a passport verification or driver’s license, using AI-powered software. This method capitalizes on the distinct characteristics of one’s face, transforming them into digital data that can be quickly analyzed and verified.
Industries are rapidly adopting this method for its blend of user-friendliness and security. During customer onboarding, for instance, users simply upload their government-issued ID and then take a selfie. The software checks this selfie against the ID to ensure the person is who they claim to be, thus preventing identity theft and unauthorized access.
Growing popularity of selfie identity verification
The embrace of selfie identity verification across various sectors is a testament to its effectiveness in reinforcing trust and security in digital interactions.
This user-friendly approach to confirming identities is rapidly becoming a cornerstone in industries like fintech, where it streamlines the onboarding of new customers.
In the gaming world, it is utilized as an additional layer of security to verify age and prevent underage use, and within the cryptocurrency sphere, it fortifies transactional security by using identity documents and ensuring that wallet holders are the true owners.
Benefits of selfie identity verification
Protection against database breaches
Selfie identity verification stands out for its direct approach to security. It minimizes the risk of database breaches by using biometric technology to compare live selfies with photo IDs, ensuring a live match and thwarting identity fraud prevention and theft.
Low-friction verification
The low-friction aspect of selfie identity verification is crucial. It simplifies the authentication process to a quick selfie, eliminating the need for multiple ID checks or complex password database verification. This simplicity enhances user compliance with verification measures, which, in turn, upholds security standards.
This innovative method of identity verification ensures a secure, swift, and user-friendly experience, allowing verification of a person’s identity with just a selfie. It’s a perfect example of how advanced real-time face detection technology can be applied to streamline and secure user verification processes across a myriad of digital platforms.
How does selfie verification work: Step-by-step process
Completing a selfie ID verification process is a straightforward process designed for security and simplicity.
Our step-by-step approach ensures a user-friendly experience for onboarding new customers or securing financial transactions. Below is a comprehensive guide to the typical selfie identity verification process.
- Capturing Government-Issued ID: You need a clear photo of the user’s government-issued identification, such as a driver’s license or passport. This step often involves using a smartphone or tablet to capture a high-quality image in good lighting.
- Uploading the ID: Next step is to upload the photo of the ID to a selfie identity verification solution.This could be a mobile app or a web portal. Ensure the image is clear and all relevant information is visible.
- Taking a Live Selfie: Following the upload, the user will be prompted to take a live selfie. This usually involves facing their device’s camera and following on-screen instructions. The aim is to capture your live physical presence, which is crucial for the next step.
- Performing Liveness Detection: The system will then perform a liveness check to ensure that the selfie is indeed live and not a photograph or video. This is where sophisticated algorithms come into play, analyzing the selfie for signs of real-time human presence.
- Face Matching: The software compares the live selfie with the photo on your uploaded ID. It uses facial recognition technology to verify that the person in the selfie and the ID are the same.
- Validation and Approval: If the comparison is successful and no discrepancies are found, the system will validate the verification process.
- Continuous Authentication: For returning users, some platforms may use the initial verification to reauthenticate users quickly, creating a smooth and secure ongoing experience.
Is selfie identity verification foolproof?
The adoption of the selfie identity verification solution has surged across industries, thanks to its ease of use and robust security features. However, like any technological solution, it is not without its vulnerabilities.
While the system offers a high degree of accuracy, it’s important to understand its limitations and the measures in place to counteract them.
Potential for false positives
A false positive in selfie identity verification occurs when the system incorrectly matches the selfie with the photo ID, despite them being of different individuals.
To mitigate this risk, advanced verification systems don’t rely on facial recognition or selfie checks alone. They incorporate multiple checks, such as document verification and liveness detection, to ensure that the person is who they claim to be.
Beware of deepfakes
Deepfake technology, which uses artificial intelligence to create realistic images and videos, poses a significant challenge to selfie identity verification systems.
To combat this, companies employ advanced face matching software capable of distinguishing between a real person and a synthetic image. These systems analyze the texture, movement, and other biometric signs to confirm the presence of a live person, thus safeguarding against deepfake attempts.
Best practices for selfie identity verification
The security and integrity of digital operations hinge on the proper implementation of identity verification practices. Here’s a closer look at the best practices for selfie identity verification, drawing from industry standards and expert insights:
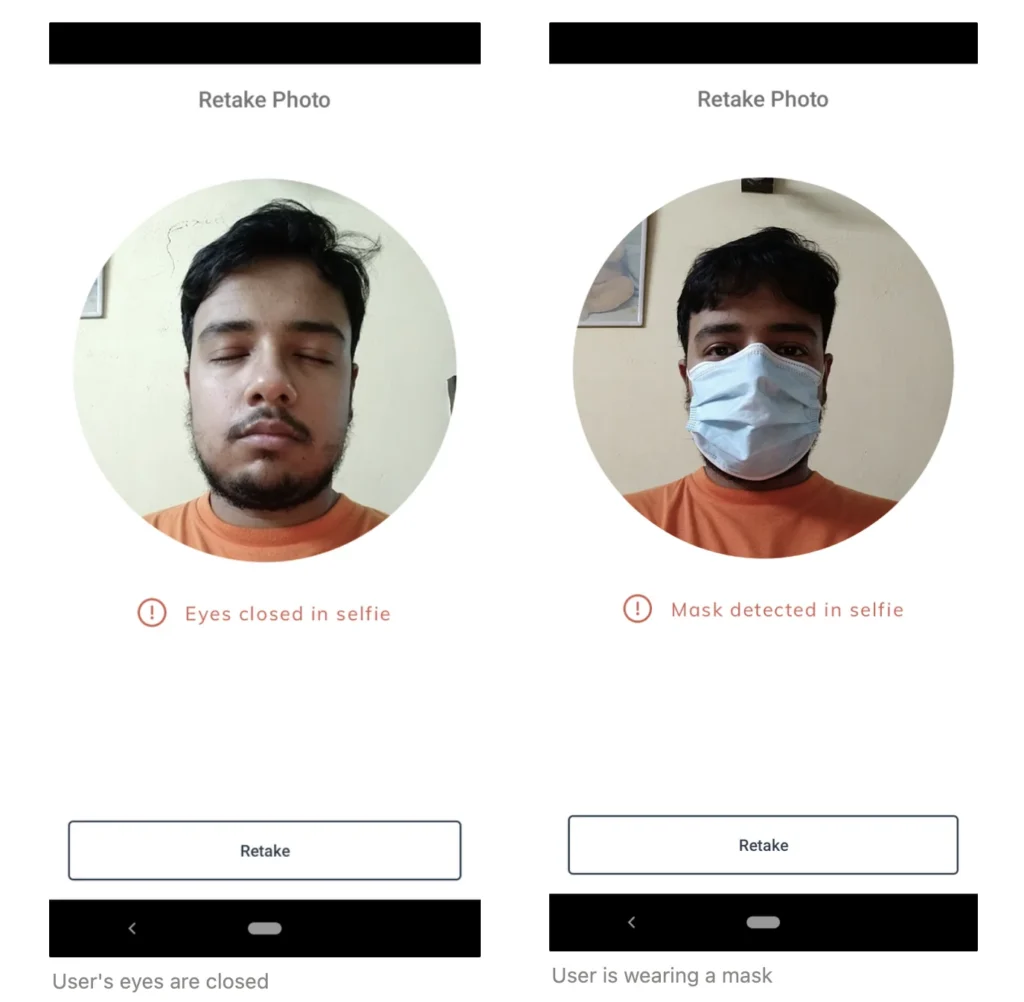
Perform liveness detection checks
Liveness checks are critical to ascertain that the individual is present in real-time and not a spoof or a static representation. Utilizing both active and passive liveness checks can provide a comprehensive safeguard. Active liveness might ask a user to perform a series of actions like:
- Speak out the text displayed on the screen
- Hold a piece of paper where they write down some verification text
- Perform gestures such as moving their head up and down, left and right, blinking, etc.
Passive liveness, on the other hand, silently analyzes the video feed for signs of life, such as subtle facial movements or texture analysis.
Use robust AI models to avoid bias
The accuracy of selfie identity verification work done is highly contingent on the AI models in use. It’s imperative to utilize AI software that is sophisticated and unbiased, especially when large volumes of verifications are processed. AI models must be trained on diverse datasets to avoid biases related to race, gender, or age, ensuring fair and equal treatment for all users.

Read more: How to Mitigate Facial Recognition Bias
Use selfie identity verification as an additional verification layer
Incorporating selfie verification as part of a multi-factor authentication process can significantly enhance security. It should complement other methods such as document verification and database checks, offering a robust multi-layered defense against identity fraud.
How to add selfie identity verification to your KYC workflow
Integrating selfie identity verification into your Know Your Customer (KYC) workflow can significantly enhance the security and integrity of sensitive data in your customer verification process.
Deploy a robust identity verification tool that has a powerful face recognition engine. For instance, HyperVerge’s face authentication has been rated in top 10 globally by NIST!
To build a comprehensive and robust KYC workflow, include a variety of verification methods:
- Document Verification: Start by verifying the authenticity of government-issued IDs or documents. This step confirms that the document is valid and has not been altered or forged.
- Email Verification: Ensure that the email address provided by the user is active and accessible. This can also help in re-verifying the identity if needed.
- Phone Verification: Similar to email, verify the phone number to ensure it is in service and owned by the user. This also adds an additional layer of security and a direct line of communication with the customer.
- Captcha Detection: Incorporate Captcha to prevent automated bots from creating accounts or accessing services, ensuring that a real person is attempting the verification.
- Trusted Identity Network: Leverage a network of verified identities, often powered by blockchain technology, to validate that the user’s provided information is trustworthy and has been verified by other reliable sources.
- Multi-Factor Authentication (MFA): Combine something the user knows (like a password), something the user has (like a phone), and something the user is (like a biometric feature) to create a layered defense against unauthorized access.
- Other Biometric Methods: Beyond selfies, leverage other biometric verification methods such as fingerprints, voice recognition, or iris scans to confirm identity. These methods provide unique physiological data that are extremely difficult to replicate or forge.
For more information, explore our detailed guide to identity verification and how HyperVerge can help.
Conclusion
By incorporating selfie verification alongside other robust methods like identity document checks, email and phone verification, Captcha, trusted identity networks, multi-factor authentication, and additional biometrics, businesses can create a multi-layered defense against identity fraud while maintaining a seamless user experience.
So, are you ready to elevate the security and efficiency of your KYC process? Look no further than HyperVerge’s advanced identity verification solutions. Get a demo now!

 US
US
 IN
IN