Paperwork is the enemy of speed. Imagine closing a million-dollar deal, but instead of sealing it instantly, you’re stuck waiting for signatures, courier delays, and piles of legal formalities. Today that’s not just inefficient—it’s unnecessary.
Digital signatures are completely rewriting how businesses and individuals handle agreements, approvals, and compliance. Whether you’re a startup finalizing contracts or a bank verifying identities, they ensure security and authenticity without the hassle of physical paperwork. But how exactly do they work?
In this blog, we break down how digital signatures in cryptography work and explore why they’re no longer just a convenience but a necessity for businesses of all sizes.
What is a digital signature in cryptography?
A digital signature is a cryptographic mechanism that ensures the authenticity and integrity of digital messages or documents.
It acts like a virtual fingerprint that uniquely identifies the sender and confirms that the content has not been altered during transmission. This is achieved through a mathematical transformation of data, using a pair of keys.
A good digital signature in cryptography example is banks that utilize digital signatures to authenticate electronic fund transfers. This ensures that the transfer is legitimate and that an authorized account holder is making it. This prevents fraud and data breach incidents.
How does it differ from handwritten signatures?
Both digital signatures and handwritten signatures fulfill the same purpose—authenticating documents. However, here are the key differences between them—
| Point of difference | Handwritten signatures | Digital signatures |
| Creation method | Created using cryptographic algorithms like hashing and encryption. | Created using cryptographic algorithms like hashing and encryption. |
| Security | Susceptible to forgery and fraud, relying on subjective assessments. | Ensure data integrity and authenticity with Public Key Infrastructure (PKI). |
| Verification process | Requires comparison with known samples, prone to human error. | Uses mathematical algorithms where the recipient verifies the signature with the signer’s public key. |
| Use cases | Common for personal letters, checks, and legal documents. | Ideal for online transactions, software distribution, and electronic contracts. |
Several key functions make digital signatures a bedrock of modern cryptography. Such functions are:
- Authentication: They verify the identity of the sender, ensuring that the message comes from a legitimate source. For example, when you receive an email with a digital signature, you can be confident it was from a claimed sender.
- Integrity: Digital signatures prevent message or document tampering. If any alteration occurs after signing, the signature will no longer be valid.
- Non-repudiation: Once a document is signed, the signer cannot deny having signed it. For instance, in legal contracts, a digital signature provides evidence that both parties agree to the terms. This prevents either party from later claiming they did not consent.
How do digital signatures work?
Digital signatures leverage cryptographic techniques, including hashing, encryption, and key pairs. Here’s how the process unfolds:
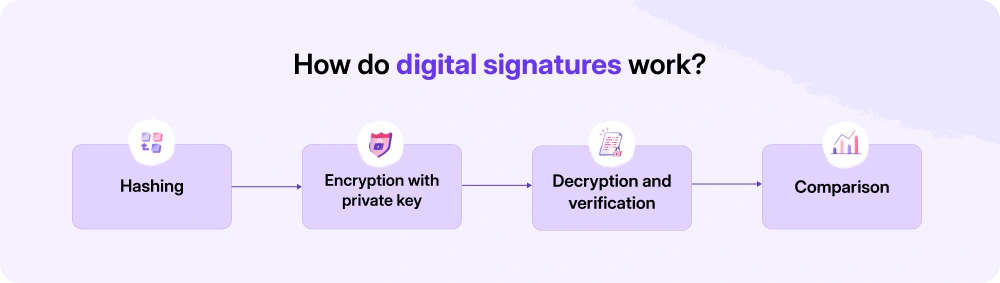
1. Hashing
The first step in creating a digital signature is to generate a unique hash value from the original data. A hash function takes an input (the document or message) and produces a fixed-size string of characters. This string is unique to that specific input.
Even a minor change in the original data will result in a completely different hash value. That’s why any alterations to the document can be detected.
2. Encryption with private key
Once the hash value is generated, it is encrypted using the sender’s private key. This encrypted hash becomes the digital signature.
The signer keeps the private key secret. It ensures only they can create a valid signature for their messages. The combination of the original message and its digital signature is then sent to the recipient.
3. Decryption and verification
Upon receiving the signed document, the recipient uses the sender’s public key to decrypt the digital signature. This process reveals the hash value that the sender had created originally.
The recipient then independently computes the hash of the received document using the same hash function.
4. Comparison
Finally, the recipient compares the decrypted hash value with their own computed hash value. If both hashes match, it confirms that:
- The message was indeed sent by the claimed sender (authentication)
- The message has not been altered during transmission (integrity)
Any discrepancy between the two hash values indicates two outcomes. Either the message has been tampered with or it was not signed by the legitimate sender.
Digital signatures make this process possible through asymmetric cryptography. This technique utilizes two keys:
- Private key: A secret key known only to the signer is used to create digital signatures.
- Public key: A publicly available key used by recipients to verify signatures.
This system ensures that while anyone can verify a signature using the public key, only the holder of the private key can create one.
Several algorithms are commonly used for generating digital signatures. The prominent ones include:
- RSA (Rivest-Shamir-Adleman): This widely used algorithm relies on the mathematical difficulty of factoring large prime numbers.
- ECDSA (Elliptic Curve Digital Signature Algorithm): This algorithm utilizes elliptic curves to provide similar security levels as RSA but with smaller key sizes, making it more efficient.
Onboard customers without risks and downtimes
with HyperVerge’s Aadhaar-based e-Sign solutions. Schedule a DemoApplications of digital signatures in India
Digital signatures have become an integral part of various sectors in India. Let’s understand how they are reshaping digital transactions across banking, e-commerce, and legal documentation.
- Use in Government services
Digital signatures are redefining government services in India. The Aadhaar-based eSign service allows citizens to sign documents electronically using their Aadhaar number and a one-time password (OTP).
This is simplifing tax filing, and government schemes application, making them more efficient. For instance, businesses can file Goods and Services Tax (GST) returns digitally, reducing paperwork and processing time.
- Applications in banking
Digital signatures have accelerated various processes in the banking sector, including loan applications, account openings, and fund transfers.
Banks are now asking customers to sign documents digitally to mitigate risks associated with forged signatures. Furthermore, digital signatures is facilitating seamless electronic communication between banks and their clients, protecting sensitive information during transmission.
- Application in e-commerce
E-commerce platforms are leveraging digital signatures to secure online transactions and build customer trust. When users make purchases or sign up for services, digital signatures authenticate their identity and protect against unauthorized access.
For example, when a customer places an order, the transaction details are signed digitally to ensure that the order is legitimate and has not been altered. Additionally, digital signatures help e-commerce businesses comply with legal requirements related to consumer protection and data privacy.
- Application in legal documentation
Digital signatures provide a legally recognized alternative to handwritten signatures under the Information Technology Act, of 2000. Professionals can use digital signatures for contracts, agreements, and other essential documents.
- Securing online transactions
Digital signatures secure online transactions by verifying the sender’s identity and ensuring that content remains unchanged during transmission through hashing, encryption, and decryption. This guarantees data integrity because any alteration to the document after signing will result in a mismatch during verification.
Advantages and limitations of digital signatures
Digital signatures offer numerous advantages that streamline processes. But they also sustain a few limitations currently. Let’s view both in detail.
Advantages
- Enhanced security and authentication
The digital signature, through a pair of keys, guarantees that only the legitimate signer can create a valid signature. Additionally, any changes made to the document after signing will invalidate the signature. This reduces fraud and forgery risk, compared to traditional handwritten signatures, which can be easily replicated.
- Reduced paperwork and faster processes
In traditional settings, signing documents involves printing, signing, scanning, and emailing or mailing physical copies. Digital signatures eliminate these steps. Users can sign documents electronically from anywhere at any time. This speeds up turnaround times for contracts, approvals, and transactions.
- Legally binding in India under the IT Act 2000
In India, digital signatures are legally recognized under the Information Technology Act, of 2000. This ensures that they hold the same legal weight as traditional handwritten signatures.
Also, note that digital signatures are enforceable in court. Hence, individuals and businesses can confidently rely on digital signatures for legal documents. This encourages their adoption across industries.
Limitations
- Dependency on infrastructure and digital literacy
Digital signatures rely heavily on a technological infrastructure. This includes internet access, secure servers, and reliable software. In regions where such infrastructure is lacking, the adoption of digital signatures can be significantly hindered.
For instance, rural areas in India may face challenges due to unreliable internet connectivity or insufficient technological resources. Moreover, digital literacy can impact the successful implementation of digital signatures. If users lack the knowledge to navigate digital signature processes, it can result in underutilization and potential security risks.
- Risks if private keys are compromised
The security of digital signatures depends on the integrity of the private key. If a private key is compromised—whether through cyberattacks, phishing schemes, or poor key management—the consequences can be severe. An attacker can forge signatures using keys. This can lead to financial fraud or identity theft.
Future of digital signatures in cryptography
As organizations increasingly adopt digital solutions, advancements in cryptographic technologies, such as quantum encryption and blockchain integration are predicted to improve the security and reliability of digital signatures.
Blockchain technology, through its decentralized and immutable nature, may help create tamper-proof records and provide clean traceability. Further, the integration of artificial intelligence (AI) could completely automate signature verification processes.
HyperVerge with its advanced AI platform remains at the forefront here—collect digital signatures of your users without error, delays, and risks. Reduce onboarding friction and drop-off rates with Aadhar e-sign solutions.
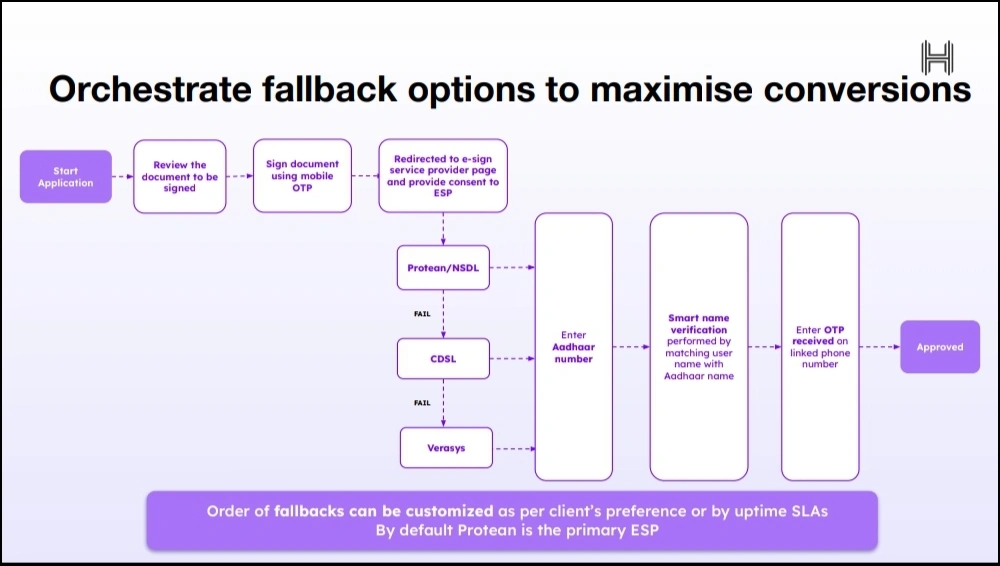
- Automatically redirect your users to other ESPs when downtimes are detected.
- Avoid fraud by matching the name against Aadhaar details and verifying OTP via a phone number linked to Aadhaar, before executing signatures.
- Build automated workflows that fit into your existing business operations and improve performance with an analytics dashboard.
Learn more about Hyperverge’s e-sign solutions here.
FAQs
1. What is a digital signature, and how does it work in cryptography?
A digital signature is a cryptographic technique that validates the authenticity and integrity of digital messages or documents using a unique hash of the document and a pair of keys.
2. What is the role of public and private keys in digital signatures?
The private key, known only to the signer, creates the digital signature by encrypting a hash of the document. Public key, on the other hand, allows anyone to verify the signature by decrypting it and comparing it to a newly computed hash of the original document.
3. How secure are digital signatures? Can they be forged?
Digital signatures are secure and make forgery difficult, as the private key remains confidential and unique to the signer. However, if a private key is compromised, an attacker can create fraudulent signatures, undermining the security of the entire system.





